IAM Solutions for Modern Enterprise
This course will provide the foundational knowledge of the IAM domain, focusing particularly on implementation of IGA solutions. Along with theoretical and conceptual knowledge, the course will also provide exposure to and hands on experiences of various IAM tools and technologies

What you will learn?
Your Questions Answered
Identity Security Essentials: Prerequisite - IT Fundamentals Required
You’ll understand its role in cybersecurity and basics like IAM, PAM, and Zero Trust.
You’ll get hands-on practice with tools like SSO, MFA, and directory services.
You’ll learn IAM setup, APIs, and the difference between on-prem and cloud solutions.
Yes, you’ll onboard apps and manage data using connectors and rules.
You’ll implement workflows, policies, and role-based access with certifications.
Course Modules
Module 01: Foundational Theory of Identity Security
Topics:
- Importance and Functions of Identity Security
- IAM and Enterprise Management
- IAM and Cybersecurity
- Identity Security and Zero Trust
- IAM, PAM, and IGA – Basic concepts
- Access Management Architecture and Tools of Trade
- Directory Servies as the backbone of IAM
- SSO and MFA — Authentication and Authorization Protocols
- Access Control Principles and Methods
Module Overview
This module covers the core concepts of identity security and its role in cybersecurity.
You’ll explore IAM, Zero Trust, SSO, MFA, and access control basics.
Module 02: Basic Architecture & Infrastructures of Identity Governance
Topics:
- Architecture and Infrastructure
- Connectivity and API
- OnPrem vs. Cloud Solutions
- Deployment, Upgrade, Migration
- Extensions and Customization
Module Overview
This module introduces IAM architecture, infrastructure, and connectivity via APIs.
You’ll compare on-prem vs. cloud solutions and learn deployment essentials.
Module 03: Hands-on Exercise: Application Onboarding and Data Aggregation
Topics:
- Aggregation Fundamentals
- Authoritative vs. Non-Authoritative Sources
- Identity Mapping and Identity Profiles
- Correlation
- Tasks
- Uses of Rules and Transforms to manipulate Data
- On- boarding applications using Different Connector Types
Module Overview
This module provides hands-on practice in onboarding applications and aggregating data.
You’ll work with connectors, rules, and identity mapping techniques.
Module 04: Hands-on Exercise: Implementing Provisioning Access Control
Topics:
- Workflows and Triggers
- Access Request and Approval
- Life-Cycle Management
- Policy Enforcement
- Role-Based Access Control
- Certifications
- Reporting and Analytics
Module Overview
This module focuses on practical skills in provisioning and access management.
You’ll implement workflows, policies, and role-based access controls.
Program Highlights
SP is a prominent player in the global Identity Access Management (IAM) sector, boasting the largest market share and a high demand for experts skilled in its software. Our SP IdentityIQ Implementation & Development training program equips you with the essential and foundational knowledge required to administer, implement, and develop within the SP IdentityIQ & Access Management Software.
96+Hour LIVE Instructors (USA Based)-Led Training
Instructor led Group Study Session Domain Theory Learning, Mock Interviews, Resume Reviews
Dedicated Lab Sessions
Career Guidance and Mentorship
Learn with Real-world Scenarios
Training Completion Certificate
Highly Interactive and Dynamic Sessions
Dedicated Session for Interview Prep
Learn from Industry Experts
Moneyback Guarantee after One Class
Extended Post Training Support
Access to Recorded Sessions
About the Course
How We Help You Succeed
About Course
SP IdentityIQ provider with a global adoption rate of 75%; its integrated governing systems deliver specific Identity Governance capabilities like compliance control, provisioning, access request, and password management in applications in leading organizations worldwide. Grab fundamental concepts and skills necessary to administer and develop in the SP IdentityIQ software ecosystem and take your career prospects to the next possible level. Gain essential SP developer skills while complementing them with effective administration knowledge to strengthen your conceptual and practical understanding of the platform.
Our SP IdentityIQ Implementation & Developer training program is specially designed with three key modules to train your skills effectively: Implementation, Administration, & Development, essentially preparing you for a wide array of SP roles. Get additional downloadable resources, SP Documents, Cloud VMs, and virtual machines necessary to enhance or complement your learning experience. Upon completing this course, you will be eligible for various SP jobs like SP IIQ developer, SP Administrator, SP IIQ expert, etc.
Course Objectives
- Understand IAM concepts and SP IdentityIQ architecture.
- Master installation and deployment procedures for IdentityIQ.
- Explore IdentityIQ business purposes and common components.
- Learn application on-boarding, account correlation, and configuration.
- Implement and manage risks, policies, and policy violations.
- Understand certification lifecycles and access review processes.
- Master Role-Based Access Control (RBAC) and role management.
- Develop troubleshooting and debugging skills.
- Configure reporting architecture and define data sources.
- Gain insights into Lifecycle Manager and access request processes.
- Create and troubleshoot workflows, including custom forms and XML content.
- Customize and monitor workflows and workflow operations.
Target Audience
SP Exam Prep Training is suitable for anyone willing to pass the certification exam. If you are:
- An aspirant looking forward to starting a career in SP
- A professional who wants to change the career domain to Identity and Access Management (IAM)
- A Software Developer or Tester
- Java Developer
- Anyone who has Java knowledge and is interested in starting their career in SP IAM
Pre-requisites
This ensures foundational knowledge of computing, cybersecurity, and IT concepts.
Course Curriculum
Part 1 of Training Administrator:
IAM overview and Its Key concepts, Product Architecture – Installation – Deployment, Overview and Product Architecture, Implementing Risks and Policies, Certifications, Roles, Troubleshooting, Debug, Console, Reporting, Lifecycle Manager
Part 2 of Training Developer:
Introduction to Workflows, IdentityIQ Default Workflows, Workflows Operation, Creation and modifying Workflows, Process Editor Tabs, Accessing the XML, XML Content, Reference Syntax, Monitoring Workflows, Components of a Form, Defining Custom Forms, Forms Models, Form Examples, Overview of Quick Links, DynamicScope, QuickLinkOption, Filter Strings and Values for search, SP Object Model, Walk through SP database, Custom Rules (Query SP objects),Certification Rules (Exclusions / Pre delegation), Object Exporter, Workgroup Exporter / Importer
SP Training Course Topics:
- IdentityIQ Business Purpose
- IdentityIQ Overview
- IdentityIQ Common Components
- Overview of an IdentityIQ Project
Product Architecture – Installation – Deployment
- Understanding the Product Architecture
- Understanding the Installation Procedure for IdentityIQ
- Understanding the Installation Procedure for SP IdentityIQ Patching
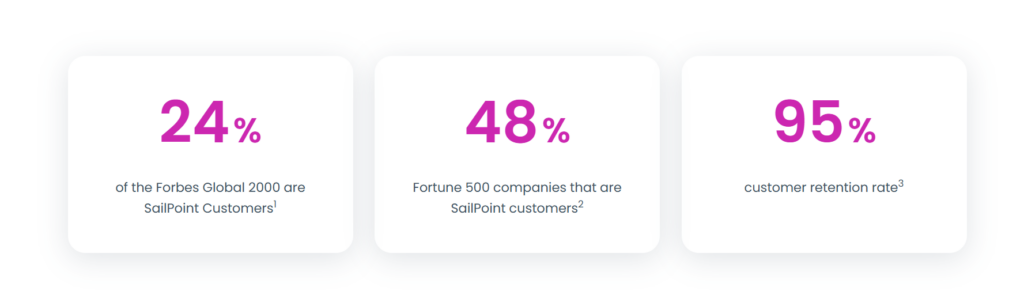
Fact Check
References
1. https://www.forbes.com/lists/global2000/ 2. https://fortune.com/ranking/fortune500/ 3. SP website data